

Convenience is paramount in the world of online banking, but this kind of premium accessibility can lead to an increased risk of data breaches. In today’s rapidly-evolving digital landscape, it’s more important than ever to keep banking information secure across your devices.
SAFEGUARDING YOUR MOBILE DEVICE
In addition to always keeping your device’s software up to date, you should configure it to require a passcode to gain access and use antivirus software where applicable (i.e., Androids, Windows, etc.). Since mobile devices have a high likelihood of being lost or stolen, you should avoid using them to store sensitive information. If sensitive data is already stored, be sure to enable encryption to secure it. Also, it’s never a good idea to jailbreak or otherwise circumvent security controls.
Before installing any apps, review the privacy policy and data access for each, and always remember to “Sign Out” or “Log Off” when you’re finished, rather than just closing the app. Disabling features like Bluetooth, Wi-Fi, and infrared when you’re not using them provides security while improving your device’s overall performance.
When Bluetooth is enabled, set your devices to “non-discoverable” as an extra precaution. If you plan on selling or trading in your device, don’t forget to delete all information before the device changes ownership. You can permanently erase all content and settings stored on your device by using a “hard factory reset.”

VERIFYING YOUR SAFETY ONLINE
Because emails, tweets, social posts, and online advertising can be riddled with suspicious links, resist the urge to click unknown links at all costs. These questionable links can take you to a different website than their labels indicate. As a safer alternative, type any address you find into your browser instead of clicking a link in an email.
While your information travels across the Internet, ensure it’s protected by submitting sensitive information only to websites that use encryption. Be cautious of unsolicited phone calls, emails, or texts directing you to a website or requesting personal information. Verify that the web address begins with “https://” (the “s” stands for “secure”) rather than just “http://”. Some browsers also display a closed padlock icon in the search bar to designate a secure connection. If a site contains certificate warnings or errors, do not trust it. These error messages could mean your connection is being intercepted or that the web server is misrepresenting its identity.
Steer clear of using public computers or public wireless access points for online banking and other activities involving sensitive information. And again, always “Sign Out” or “Log Off” of password-protected websites when you’re finished browsing to prevent unauthorized access. Simply closing the browser window may not actually end your session.
PROTECTING YOUR PC
Frequently updating your software is the key to shielding your computer from online threats. Update your computer’s operating system and other installed software (e.g., web browsers, Adobe Flash Player, Adobe Reader, Java, Microsoft Office, etc.) to ensure you’re equipped with the latest security patches. If the software supports it, automate the updates so you have one less thing to worry about. Along with real-time scanning, you should schedule regular scans of your computer and maintain active and up-to-date antivirus protection provided by a reputable vendor. And of course, make sure your computer requires a password to gain access, and consistently log off or lock it when not in use.
If you suspect your computer is infected with malware, discontinue using it for banking, shopping, or other activities involving sensitive information. Install security software and/or consult professional help to find and remove the damaging malware. You can also use firewalls on your local network to add another layer of protection for all the devices that connect through the firewall (e.g., PCs, smartphones, and tablets). As a final line of defense, use a cable lock to physically secure your laptop when it’s stored in an untrusted location.
GUARDING YOUR ACCOUNTS WITH PASSWORDS
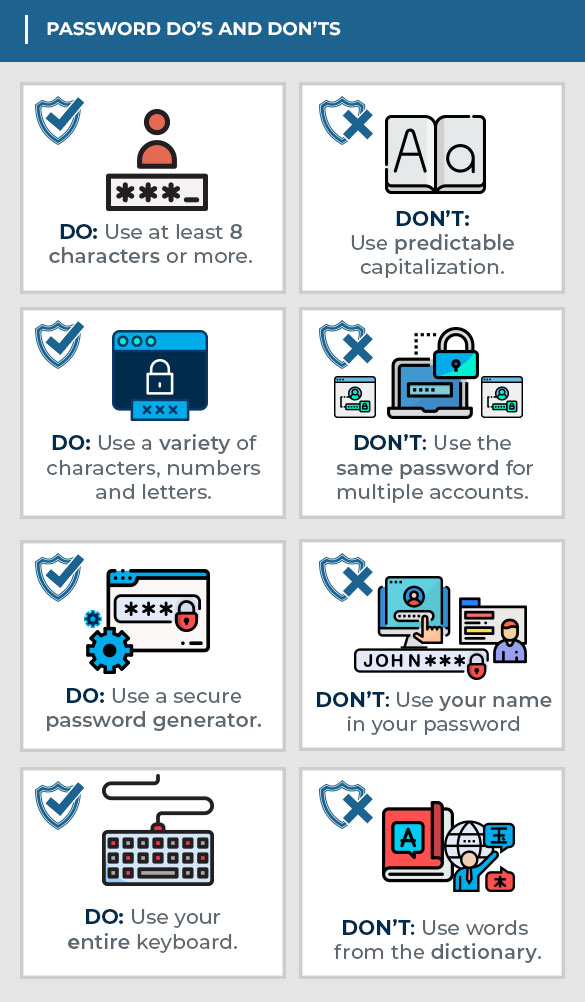
A strong password is the ultimate measure in preserving the security of your personal data. Create a unique iteration for each of the different systems and websites you use. Otherwise, one breach can leave all of your accounts vulnerable. Your password is sacrosanct—never share it over the phone, in texts, by email, or in person. If you are asked for your password, it’s probably a scam.
Choose a password you can remember without writing it down. If you feel you must write it down, store it in a secure location. Be sure your password is as unpredictable as possible by using a combination of lowercase letters, capital letters, numbers, and special characters. The longer the password, the tougher it is to crack, so try to utilize at least eight characters. Every additional character exponentially strengthens your password.
Refrain from using obvious passwords such as:
- Names (e.g., your name, family members’ names, business name, user name, etc.)
- Dates (e.g., birthdays, anniversaries, etc.)
- Dictionary words
Get your hands on our plan.
Ready to get started? Download and print the complete Business Blueprint to keep, read and use as a continued resource.
